AWS IAM (Identity & Access Management) visualization
- Troy Dieter
- Aws
- September 21, 2021
Table Of Contents
Overview
Over the years of utilizing AWS (Amazon Web Services), I find myself:
- Evaluating existing IAM roles, policies, trust relationships and any SSO federation granting role assumption or policies
- Migrating from one account within an AWS Organization to another (or a personal account to personal account) and need to understand the impact
- Deep-diving on new tools to visualize IAM policies
Here arises PMapper, an open-source project maintained by NCCGroup.
PMapper - Intro
Principal Mapper (PMapper) is a script and library for identifying risks in the configuration of AWS Identity and Access Management (IAM) for an AWS account or an AWS organization. It models the different IAM Users and Roles in an account as a directed graph, which enables checks for privilege escalation and for alternate paths an attacker could take to gain access to a resource or action in AWS.
PMapper includes a querying mechanism that uses a local simulation of AWS’s authorization behavior. When running a query to determine if a principal has access to a certain action/resource, PMapper also checks if the user or role could access other users or roles that have access to that action/resource. This catches scenarios such as when a user doesn’t have permission to read an S3 object, but could launch an EC2 instance that can read the S3 object.
TL;DR: A nifty tool written in Python3, to visualize who has access to what in the accounts you analyze.
PMapper - Requirements
PMapper runs off of Python3.5+ and requires the following:
- pydot (grab it from PIP)
- graphviz (available for Ubuntu\Debian users in APT, other distributions including Windows available via the link)
- aws-cli with the
aws configurecommand executed to ensure a profile is built with credentials
PMapper - Installation
Once you’ve satisfied the requirements, grab pmapper from PIP as well.
PMapper - Commands
PMapper has a wide-array of available commands and customization arguments:
tdieter@DESKTOP-GNNVV9P:/mnt/c/temp/principalmapper$ pmapper -h
usage: pmapper [-h] [--profile PROFILE] [--account ACCOUNT] [--debug]
{graph,orgs,query,argquery,repl,visualize,analysis} ...
optional arguments:
-h, --help show this help message and exit
--profile PROFILE The AWS CLI (botocore) profile to use to call the AWS API.
--account ACCOUNT When running offline operations, this parameter determines which account to act against.
--debug Produces debug-level output of the underlying Principal Mapper library during execution.
subcommand:
The subcommand to use among this suite of tools
{graph,orgs,query,argquery,repl,visualize,analysis}
Select a subcommand to execute
graph Pulls information for an AWS account's use of IAM.
orgs Pulls information for an AWS Organization
query Displays information corresponding to a query
argquery Displays information corresponding to a query
repl Runs a REPL for querying
visualize Generates an image representing the AWS account
analysis Analyzes and reports identified issues
PMapper - Demo
For this demonstration, we’ll graph the default environment:
pmapper graph create && pmapper visualize --filetype svg
The below GIF shows installation of the requirements and PMapper on Ubuntu 20.04.3 LTS along with the visualization, based on my default profile in ~.aws\credentials
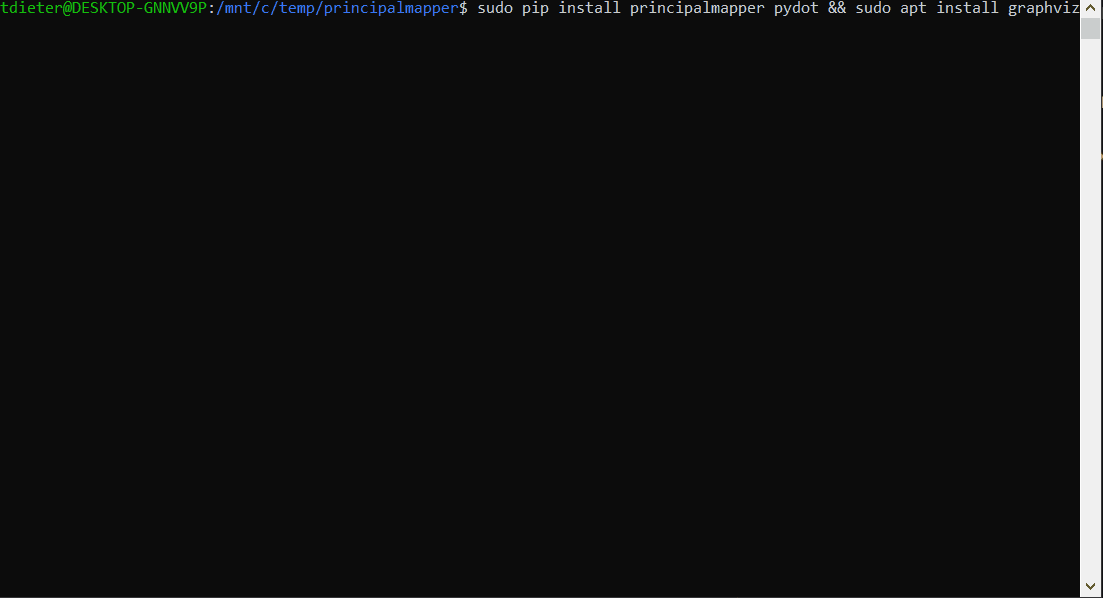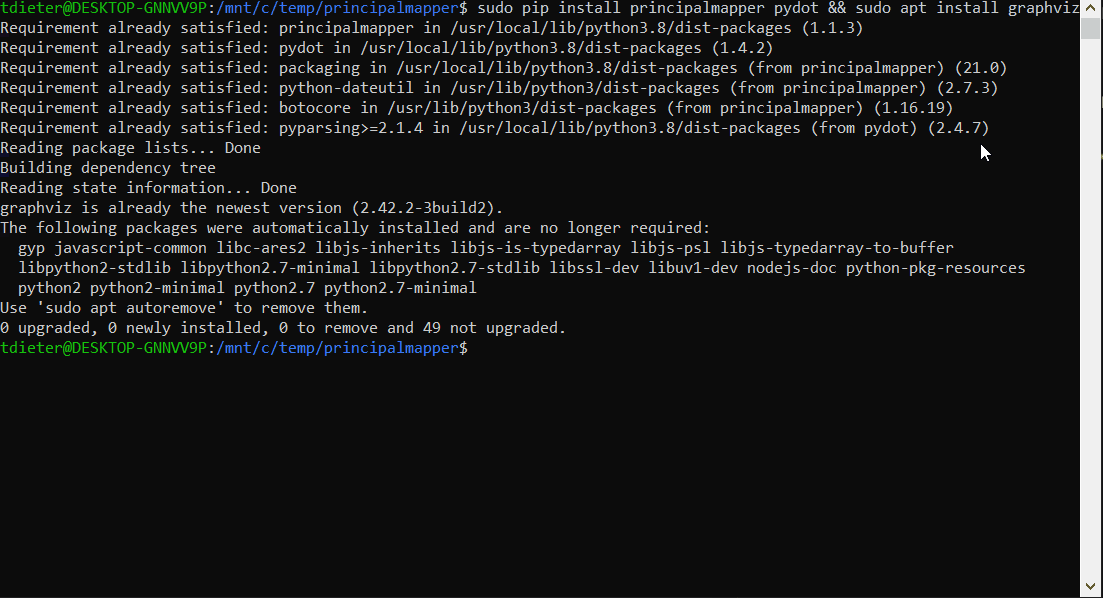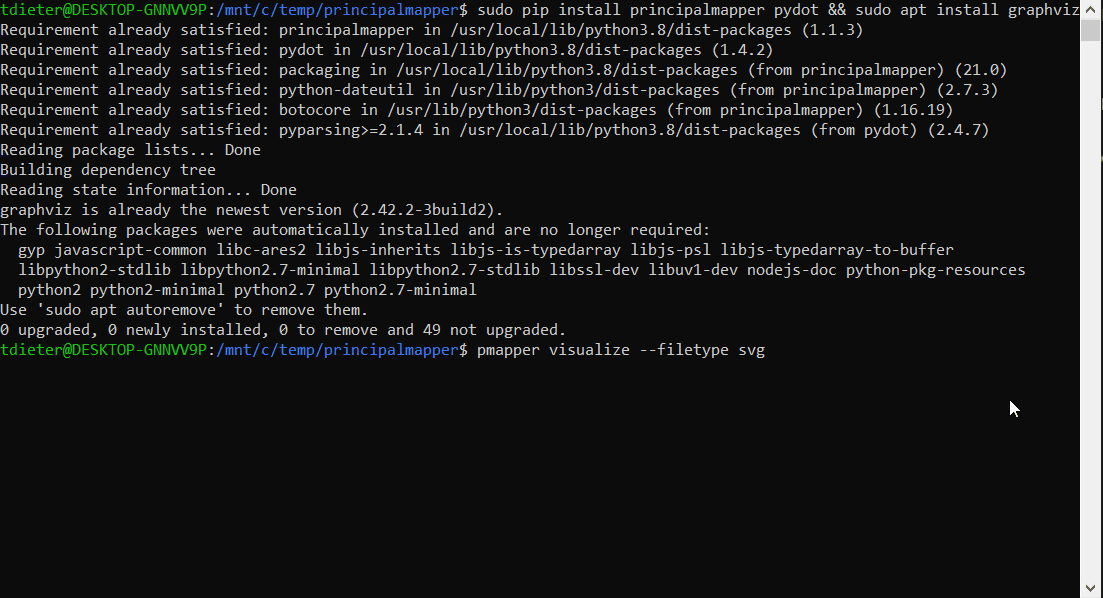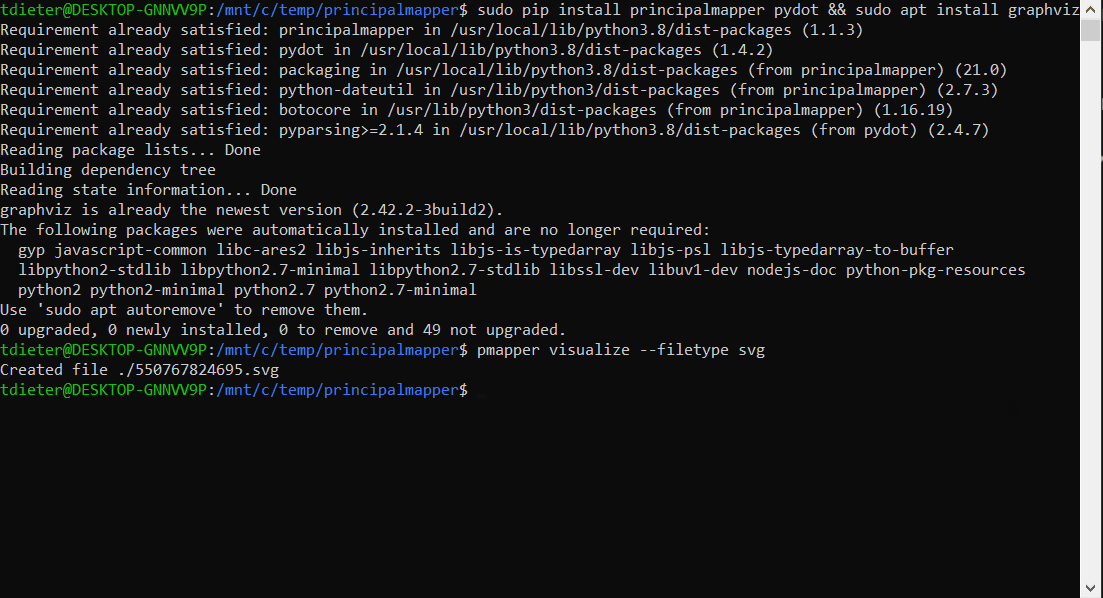
PMapper - Visualization
The commands ran previously will output a .svg file that can be viewed within a browser. It will be created in the same directory you executed the command in.
The above GIF demonstrates the relationship(s) between the AWS IAM roles, policies within this account.
PMapper - Recap
These types of open-source projects that help “call out” certain over-privileged roles I am quite fond of. It also helps to demonstrate the reach that a vendor (that may have a trust relationship established within a cross-account role) may have.
Appendix
If you are looking for a tool that also provides actionable items, I recommend Self-Service Security Assessment and utilizing the Security pillar of the AWS-Well Architected framework.
The AWS prescriptive guidance website is a great resource for related matters.